Back to: ASP.NET Core Web API Tutorials
Authorization Filters in ASP.NET Core Web API
In this article, I will discuss Authorization Filters in ASP.NET Core Web API Applications with Examples. Please read our previous article discussing the basic concepts of Filters in ASP.NET Core Web API Applications. Authorization is a critical part of securing Web APIs. In ASP.NET Core Web API, filters offer a clean and structured way to manage authorization logic at the request processing level.
What is an Authorization Filter in ASP.NET Core Web API?
Authorization Filters in ASP.NET Core Web API are specialized filters that execute before the main API logic runs. Their primary job is to verify whether the current user has the correct permissions to access a particular API endpoint (action or controller).
- If the user is authorized, the filter allows the request to continue.
- If the user is not authorized (e.g., not logged in, lacks required roles or claims), the filter blocks the request and returns an appropriate error, typically HTTP 401 (Unauthorized, if the user is not authenticated) or 403 (Forbidden, if the user is authenticated but not permitted).
In simple terms, think of an Authorization Filter as a strict security guard stationed at the door of every restricted area in a building. Only those with the right credentials can enter. For a better understanding, please have a look at the following image:
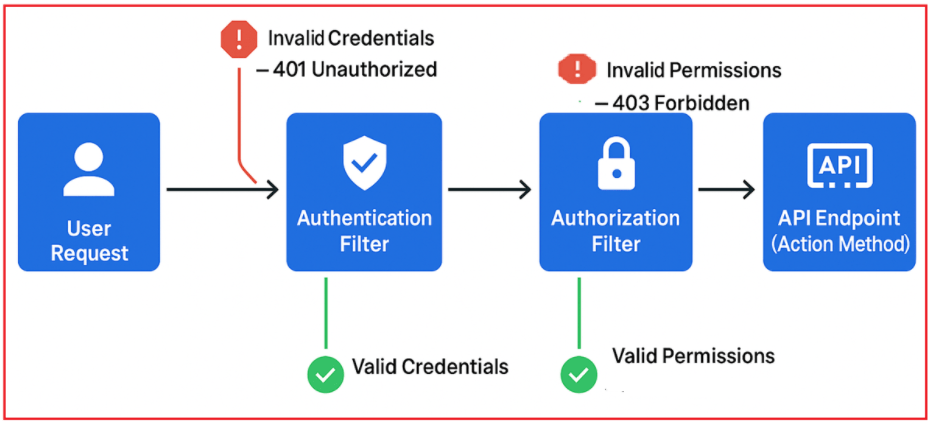
How Does Authorization Filter Work in ASP.NET Core Web API
Step-1: User Request:
- The process begins when a user sends a request to the Web API (e.g., trying to access a resource or perform an action).
Step-2: Authentication Filter:
This filter checks the user’s credentials (such as username/password, tokens, etc.) to verify the user’s identity.
- If the credentials are invalid, it immediately returns a 401 Unauthorized response, indicating that the user is not authenticated. This path is shown with a red arrow going upwards to the error message labeled “Invalid Credentials”.
- If the credentials are valid, the request proceeds to the next step (shown with a green arrow going downwards labeled “Valid Credentials”).
Step-3: Authorization Filter
Once authenticated, this filter checks if the user has the correct permissions to access the requested API endpoint or perform the requested action.
- If the permissions are invalid or insufficient, it returns a 403 Forbidden response, meaning the user is authenticated but not authorized to perform the action. This path is shown with an orange arrow going upwards to the error message labeled “Invalid Permissions”.
- If the permissions are valid, the request proceeds to the final step (shown with a green arrow going downwards labeled “Valid Permissions”).
Step-4: API Endpoint (Action Method)
After successful authentication and authorization, the request reaches the API endpoint, where the actual action method executes and processes the request accordingly.
Example 1: The VIP Club
Imagine a VIP club that only lets in people who have a special VIP pass.
- The club’s door is the API endpoint (the action you want to execute).
- The bouncer at the door is the Authorization Filter.
- When someone tries to enter, the bouncer checks if they have a VIP pass (authorization).
- If they do have the pass, they get in and enjoy the club (the API action runs).
- If they don’t have the pass, the bouncer refuses entry, and they are not allowed in (the request is blocked with an error).
The bouncer (authorization filter) doesn’t care who you are until you prove you’re on the list. No pass, no entry. This is exactly how authorization filters work—they protect sensitive resources from unauthorized users.
Example 2: Movie Theater Ticket Check
Think of a movie theater where you need a valid ticket to watch a specific show.
- The gate to the theater is the API endpoint.
- The security guard checking tickets is the Authorization Filter.
- Before you enter, the guard verifies your ticket to see if it matches the movie and showtime.
- If your ticket is valid for this show (you have the right permission/role), you are allowed inside (the API action executes).
- If your ticket is invalid or missing, you are stopped at the gate (the request is denied).
The security guard ensures that only those with valid tickets (permissions) can watch the movie (use the protected resource). This ensures only the right users get access to the right features.
What is Authentication?
Authentication is the process of confirming the identity of a user who is trying to access a system. It answers the critical question: “Who are you?” When a user tries to access a system or application, authentication confirms their identity using credentials such as usernames and passwords, security tokens, or biometric data like fingerprints or facial recognition.
In ASP.NET Core, once a user is successfully authenticated, the framework creates a ClaimsPrincipal object stored in the HttpContext.User object. This object carries the authenticated user identity and claims (like their user ID, email, or roles).
What is Authorization?
Authorization is the process of deciding what an authenticated user is allowed to do. It answers the question: “What permissions or rights do you have?” After a user’s identity is verified (authenticated), authorization checks determine whether the user has the necessary permissions or roles to access specific resources or perform particular actions. ASP.NET Core supports role-based, policy-based, and claims-based authorization to implement this.
In ASP.NET Core, once the user is authenticated, the HttpContext.User is populated with identity and claims. The authorization layer evaluates policies, roles, or custom rules based on associated claims to decide if that user can access a particular controller action, resource, or operation. If the user lacks the required permission, you will typically see an HTTP 403 (Forbidden) response.
Example: IT Company Gate with Biometrics – Authentication
Think of an IT company campus with various sections such as Reception, HR Room, Accounts Section, Server Room, Cafeteria, and Admin Room:
- At the entrance gate, employees use a biometric system (like fingerprint or facial recognition).
- This biometric system checks the employee’s credentials against a stored database.
- If the employee’s identity is confirmed (valid credentials), they can enter the campus. (ASP.NET Core issues you an authenticated user context, i.e., creates a ClaimsPrincipal object, which is stored in HttpContext.User object).
- If the match does not occur, the gate stays locked (the request is rejected with a 401), and the user never reaches any of the office areas (controllers/actions).
For a better understanding, please have a look at the following diagram:
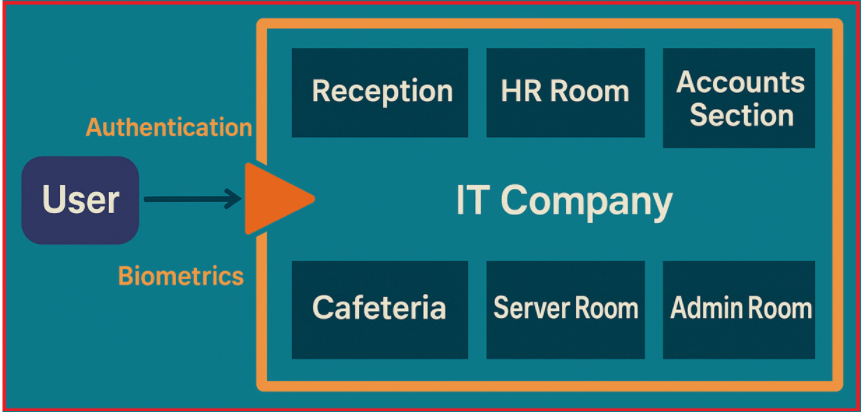
Authentication is all about this identity check at the gate. It doesn’t care what the employee can do or which rooms they can access; it only ensures that the person trying to enter is really who they claim to be.
Example: IT Company Campus Access – Authorization
Consider the IT company campus, which has multiple sections, such as Reception, HR Room, Accounts Section, Server Room, Cafeteria, and Admin Room. Once an employee passes biometric verification at the gate (authentication), they enter the campus.
- Authorization then decides which sections of the company the employee can access.
- For example, User 1 might have permission to enter the Reception and Cafeteria but not the Admin Room.
- User 2 might be authorized to access the Accounts Section and Admin Room, but not the Server Room.
- A guest may be limited to only the Reception.
For a better understanding, please have a look at the following diagram:

Each door inside the campus checks the employee’s role or privileges before unlocking. Even if you are inside the company, you can only go to the rooms you are authorized for. That’s exactly how an authorization filter or policy works in our Web API—protecting specific endpoints or resources based on what the authenticated user is entitled to access.
How Do We Implement Authorization Filters in ASP.NET Core Web API?
We need to follow the steps below:
- Built-in: Use [Authorize] attribute on controllers or actions to enforce authorization using roles, policies, or claims.
- Custom: Implement IAuthorizationFilter or IAsyncAuthorizationFilter interfaces for complex, business-specific logic.
- Registration: Filters can be registered globally (apply everywhere) or locally (specific controller/action).
The authorization filter inspects the current user’s claims, roles, or other contextual info to decide whether to allow the request to continue.
[Authorize] and [AllowAnonymous] Attributes in ASP.NET Core Web API:
By default, in the ASP.NET Core Web API applications, all the action methods of all controllers can be accessed by both authenticated and anonymous users. However, if you want the action methods to be available only for authenticated and authorized users, you need to use the Authorization Filter in ASP.NET Core MVC. ASP.NET Core provides two built-in attributes, [Authorize] and [AllowAnonymous], that can be used as Authorization filters.
- [Authorize]: This attribute enforces authorization on the controller or action. When applied, only authenticated users who meet specified roles or policies can access the endpoint. For example, [Authorize] means only logged-in users can access. [Authorize(Roles = “Admin”)] means only Admin role users can access.
- [AllowAnonymous]: This attribute allows unauthenticated access to a controller or action, even if a global or controller-level [Authorize] is applied. For example, a public login or registration endpoint uses [AllowAnonymous] so anyone can access it.
Implementing Authorization Filters in ASP.NET Core Web API:
Now, we will develop an ASP.NET Core Web API application to demonstrate how to secure REST API endpoints using JWT-based authentication and built-in authorization filters. It allows users to log in with their credentials to obtain a JWT token. This token is then required to access protected endpoints. The application will show how to restrict access to API resources using attributes like [Authorize], [Authorize(Roles = “…”)], and [AllowAnonymous], covering common real-world scenarios:
- Public endpoints: Open to everyone, no authentication.
- Authenticated endpoints: Require a valid JWT token.
- Single-role access: Only users with a specific role (e.g., Admin).
- Multiple roles (AND logic): Users must have all specified roles.
- Multiple roles (OR logic): Users with any of several roles can access.
These patterns mirror the security requirements found in most enterprise web APIs.
ASP.NET Core Web API Project Setup
First, create a new ASP.NET Core Web API Project with the name AuthorizationFilterDemo. We will use JWT (JSON Web Tokens) for authentication. So, please install the following JwtBearer NuGet Package, which is required for JWT Authentication in an ASP.NET Core application, by executing the below command in the Package Manager Console. This package enables JWT bearer token authentication middleware. Please install the version compatible with your .NET version.
Install-Package Microsoft.AspNetCore.Authentication.JwtBearer
Add JWT Secret Key in Configuration:
Please modify the appsettings.json file as follows. Here, we are adding a key that will be used to generate and validate the JWT token. The SecretKey will also be used to sign JWT tokens. For better security, use environment variables or secret managers in production.
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft.AspNetCore": "Warning"
}
},
"AllowedHosts": "*",
"JwtSettings": {
"SecretKey": "d3011f8b98bbc1aa1c4ff1a7d4864fc72d9ee150bd682cf4e612d6321f57821d"
}
}
Please use the following site to generate the JWT Secret key.
https://jwtsecret.com/generate
Add JWT Authentication Services and Middleware Components:
Next, we need to configure JWT Authentication Services into the dependency injection container, and we also need to add the authentication middleware components to the request processing pipeline. So, please modify the Program class as follows. The following code is self-explained, so please read the comment lines for a better understanding.
using Microsoft.AspNetCore.Authentication.JwtBearer;
using Microsoft.IdentityModel.Tokens;
using System.Text;
namespace AuthorizationFilterDemo
{
public class Program
{
public static void Main(string[] args)
{
var builder = WebApplication.CreateBuilder(args);
// Read the JWT secret key from the appsettings.json configuration file.
// This key will be used to sign and validate JWT tokens.
var jwtSettings = builder.Configuration.GetSection("JwtSettings");
var secretKey = jwtSettings["SecretKey"] ?? "d3011f8b98bbc1aa1c4ff1a7d4864fc72d9ee150bd682cf4e612d6321f57821d";
// Register MVC controllers with the application.
// Also, configure JSON options to keep property names as defined in the C# models.
builder.Services.AddControllers()
.AddJsonOptions(options =>
{
// Disable camelCase in JSON output, preserve property names as defined in C# classes
options.JsonSerializerOptions.PropertyNamingPolicy = null;
});
// Register Authentication with JWT Bearer scheme
builder.Services.AddAuthentication(options =>
{
// These two options set JWT Bearer as the default scheme for authentication and challenge.
// This means the middleware will look for JWT tokens in incoming requests by default.
// Set the default scheme used for authentication — this means how the app will try to authenticate incoming requests
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
// Set the default challenge scheme — this is how the app will challenge unauthorized requests
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
})
.AddJwtBearer(options =>
{
// Configure parameters for validating incoming JWT tokens
options.TokenValidationParameters = new TokenValidationParameters
{
// Do NOT validate the issuer (the token's "iss" claim)
ValidateIssuer = false,
// Do NOT validate the audience (the token's "aud" claim)
ValidateAudience = false,
// Ensure the token's signature matches the signing key (to verify token integrity)
ValidateIssuerSigningKey = true,
// The key used to sign tokens — must match the key used to generate tokens
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(secretKey)) // Use a symmetric key from configuration for token validation.
};
});
//Define a policy
builder.Services.AddAuthorization(options =>
{
options.AddPolicy("AdminAndManager", policy =>
policy.RequireRole("Admin") // must have Admin
.RequireRole("Manager") // AND must also have Manager
);
});
builder.Services.AddEndpointsApiExplorer();
builder.Services.AddSwaggerGen();
var app = builder.Build();
// Configure the HTTP request pipeline.
if (app.Environment.IsDevelopment())
{
app.UseSwagger();
app.UseSwaggerUI();
}
app.UseHttpsRedirection();
// Add authentication middleware to validate JWT tokens in incoming requests.
app.UseAuthentication(); // MUST come before UseAuthorization
// Add authorization middleware to check user permissions for accessing resources.
app.UseAuthorization();
app.MapControllers();
app.Run();
}
}
}
What is DefaultAuthenticateScheme?
It defines the authentication handler to be used by default when authenticating incoming requests. Here, it means the app will use JWT Bearer Authentication to validate tokens on incoming requests automatically.
What is DefaultChallengeScheme?
Defines the authentication scheme used when the app needs to challenge unauthorized requests (e.g., return a 401 response asking for credentials). Setting this ensures that when an unauthenticated user tries to access a protected resource, the app knows to challenge using JWT bearer token rules.
Create the User Model
First, create a folder named Models at the project root directory. Then, inside the Models folder, add a class named User.cs and copy and paste the following code. This model will store the user information. We will use in-memory objects to store the user list. Roles are stored as comma-separated strings (e.g., “Admin, Manager”).
namespace AuthorizationFilterDemo.Models
{
public class User
{
//Unique Id of the user
public int Id { get; set; }
//Name of the user
public string Name { get; set; } = null!;
// Username of the user
public string Email { get; set; } = string.Empty;
// Password for demo only (in real apps, store hashed passwords)
public string Password { get; set; } = string.Empty;
// Roles assigned to the user, comma-separated
public string Roles { get; set; } = string.Empty;
}
}
Creating LoginDTO:
To generate the JWT Token, we need the user’s email and password, and for this, we need a DTO. So, inside the Models folder, create a class file named LoginDTO.cs and then copy and paste the following code.
using System.ComponentModel.DataAnnotations;
namespace AuthorizationFilterDemo.Models
{
public class LoginDTO
{
[Required(ErrorMessage = "Email is required.")]
[EmailAddress(ErrorMessage = "Invalid email format.")]
public string Email { get; set; } = null!;
[Required(ErrorMessage = "Password is required.")]
[MinLength(6, ErrorMessage = "Password must be at least 6 characters long.")]
public string Password { get; set; } = null!;
}
}
Create AuthController for Token Generation:
For demonstration, create an API Controller to authenticate users and generate JWT tokens. So, create a new API Empty Controller named AuthController within the Controllers folder and then copy and paste the following code. The user needs to call the Login endpoint by providing valid credentials to get the JWT token.
using AuthorizationFilterDemo.Models;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Mvc;
using Microsoft.IdentityModel.Tokens;
using System.IdentityModel.Tokens.Jwt;
using System.Security.Claims;
using System.Text;
namespace AuthorizationFilterDemo.Controllers
{
[ApiController]
[Route("api/[controller]")]
public class AuthController : ControllerBase
{
private readonly IConfiguration _configuration;
// In-memory hardcoded users list for demo (simulate a user database)
private readonly List<User> _users = new List<User>()
{
new User {Id = 1, Email ="Alice@Example.com", Name = "Alice", Password = "alice123", Roles = "Admin,Manager" },
new User {Id = 2, Email ="Bob@Example.com", Name = "Bob", Password = "bob123", Roles = "User" },
new User {Id = 3, Email ="Charlie@Example.com", Name = "Charlie", Password = "charlie123", Roles = "Manager,User" }
};
public AuthController(IConfiguration configuration)
{
_configuration = configuration;
}
// This endpoint is accessible by anyone, even unauthenticated users
[HttpPost("login")]
[AllowAnonymous]
public IActionResult Login([FromBody] LoginDTO login)
{
// Find a user in our hardcoded list that matches the provided email and password (case-insensitive email check)
var user = _users.FirstOrDefault(u =>
u.Email.Equals(login.Email, StringComparison.OrdinalIgnoreCase)
&& u.Password == login.Password);
if (user == null)
{
// If no matching user, credentials are invalid — respond with 401 Unauthorized status code
return Unauthorized("Invalid username or password");
}
// Create a list of claims to embed inside the JWT token for this user
var claims = new List<Claim>
{
// Claim to identify the user by their email address
new Claim(ClaimTypes.Name, user.Email),
// Custom claim with user's unique Id
new Claim("UserId", user.Id.ToString()),
};
// Add claims for each role assigned to the user (roles are comma-separated string)
var roles = user.Roles.Split(',', StringSplitOptions.RemoveEmptyEntries);
foreach (var role in roles)
{
// Add a role claim for each role
claims.Add(new Claim(ClaimTypes.Role, role.Trim()));
}
// Generate a symmetric security key from the secret configured in appsettings.json
var secretKey = _configuration.GetValue<string>("JwtSettings:SecretKey") ?? "d3011f8b98bbc1aa1c4ff1a7d4864fc72d9ee150bd682cf4e612d6321f57821d";
var key = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(secretKey));
// Specify signing credentials using HMAC SHA256 algorithm and the generated key
var creds = new SigningCredentials(key, SecurityAlgorithms.HmacSha256);
// Create a JWT token embedding the claims, with no issuer/audience for simplicity, and expiration set to 30 minutes from now
var token = new JwtSecurityToken(
issuer: null, // No specific issuer specified.
audience: null, // No specific audience specified.
claims: claims,
expires: DateTime.UtcNow.AddMinutes(30), // Token valid for 30 minutes
signingCredentials: creds);
// Serialize the JWT token to a string
var tokenString = new JwtSecurityTokenHandler().WriteToken(token);
// Return the JWT token string as JSON to the client
return Ok(new { Token = tokenString });
}
}
}
Implement Resource Controller to Demonstrate Authorization Filters
The ProductController serves as a demonstration resource controller to showcase how ASP.NET Core Authorization Filters work in practice. It provides multiple API endpoints with different access requirements:
- A public endpoint accessible by everyone, no authentication needed.
- An endpoint accessible by any authenticated user, regardless of role.
- An endpoint restricted to users with the Admin role.
- An endpoint requiring the user to have both Manager AND User roles.
- An endpoint allowing users with either Manager OR User roles.
By calling these endpoints with or without a JWT token, you can observe the effect of [AllowAnonymous], [Authorize], and [Authorize(Roles=”…”)] attributes and how role-based access control is enforced. So, create a new API Empty controller named ProductsController within the Controllers folder and then copy and paste the following code.
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Mvc;
namespace AuthorizationFilterDemo.Controllers
{
[ApiController]
[Route("api/[controller]")]
public class ProductController : ControllerBase
{
// Public endpoint - no authentication required
[HttpGet("public")]
[AllowAnonymous] // Allows anyone (even unauthenticated users) to access this endpoint
public IActionResult Public()
{
return Ok("This is a public endpoint accessible to everyone.");
}
// Authenticated users only - no role restriction
[HttpGet("authenticated")]
[Authorize] // Requires a valid JWT token (any authenticated user)
public IActionResult Authenticated()
{
return Ok($"Hello {User.Identity?.Name}, you are authenticated.");
}
// Single Role Authorization - Admin only
[HttpGet("admin-only")]
[Authorize(Roles = "Admin")] // Only users with "Admin" role can access this endpoint
public IActionResult AdminOnly()
{
return Ok("This endpoint is restricted to Admin role users only.");
}
// Multiple Roles - AND Logic (User must have both Manager and Admin)
[HttpGet("manager-and-admin")]
[Authorize(Roles = "Manager")] // User must have "Manager" role
[Authorize(Roles = "Admin")] // User must ALSO have "Admin" role
public IActionResult ManagerAndAdmin()
{
return Ok("You must have BOTH Manager AND Admin roles to access this endpoint.");
}
// Multiple Roles - OR Logic (User must have Manager OR User)
[HttpGet("manager-or-user")]
[Authorize(Roles = "Manager,User")] // User needs at least one of these roles
public IActionResult ManagerOrUser()
{
return Ok("You have either Manager OR User role - access granted.");
}
}
}
Testing Each Endpoint with Postman
Obtain JWT Token
Request:
POST /api/auth/login
Body (raw JSON):
{
“Email”: “Alice@Example.com”,
“Password”: “alice123”
}
Outcome:
Returns { “Token”: “<JWT_TOKEN>” }
Save this token for use in subsequent requests in the Authorization header as:
Authorization: Bearer <token>
Public Endpoint
Request: GET /api/product/public
No Authorization header needed
Outcome:
200 OK
“This is a public endpoint accessible to everyone.”
Authenticated Endpoint
Request: GET /api/product/authenticated
Headers: Authorization: Bearer <JWT_TOKEN>
Outcome:
200 OK
Hello Alice@Example.com, you are authenticated.
If the token is missing or invalid: 401 Unauthorized
Admin-only Endpoint
Request: GET /api/product/admin-only
Headers: Authorization: Bearer <JWT_TOKEN>
Outcome:
If logged in as Alice (Admin):
200 OK
“This endpoint is restricted to Admin role users only.”
If logged in as Bob (User): 403 Forbidden
Manager-and-Admin Endpoint (AND Logic)
Request: GET /api/product/manager-and-admin
Headers: Authorization: Bearer <JWT_TOKEN>
Outcome:
If the user has both roles (e.g., Alice):
200 OK
“You have BOTH Manager AND Admin roles – access granted.”
If the user has only one: 403 Forbidden
Manager-or-User Endpoint (OR Logic)
Request: GET /api/product/manager-or-user
Headers: Authorization: Bearer <JWT_TOKEN>
Outcome:
If the user has either role (Bob, Charlie, Alice):
200 OK
“You have either Manager OR User role – access granted.”
If the user has neither: 403 Forbidden
How Do We Apply an Authentication Filter Globally in ASP.NET Core Web API?
To apply an authentication filter globally in ASP.NET Core Web API, we need to ensure that all controllers and actions require authentication by default, unless explicitly overridden using the [AllowAnonymous] attribute.
In ASP.NET Core, the [Authorize] attribute is actually an authorization filter; it ensures that authentication is required before authorization is checked. To apply authorization globally, we need to configure it in the Program.cs when adding controllers, as follows.
builder.Services.AddControllers(options =>
{
// Apply AuthorizeFilter globally
options.Filters.Add(new AuthorizeFilter());
});
All controllers and actions will now require authentication by default. You can still use [AllowAnonymous] on specific endpoints (like login or public resources) to opt them out of authentication.
When Should We Use Authorization Filters in ASP.NET Core Web API?
Authorization filters are a powerful tool to enforce security policies at the API level. Use them whenever you need to control who can access what in your Web API. Here are key scenarios where authorization filters are essential:
Protecting Sensitive Data
Some API endpoints expose confidential or sensitive information (e.g., user profiles, financial data, or admin reports). Unauthorized access to these endpoints can lead to data breaches or misuse.
- Example: In a banking API, only users with the role AccountHolder can access their own account details, while users with the role BankManager can access reports for all accounts. Authorization filters ensure only the right users see the appropriate data.
Role-Based Access Control (RBAC)
Different types of users should have different permissions. Authorization filters help you allow or deny access to API endpoints based on the user’s role (like Admin, Manager, Employee, Customer, etc.).
- Example: In an e-commerce API, only users with the Admin role can add or remove products, whereas users with the Customer role can only view products and place orders. Authorization filters prevent customers from performing admin-only actions.
Centralized Permission Logic
Instead of writing the same permission-checking code in multiple places, you can put all your authorization logic in one place (the filter). This makes your code cleaner, easier to maintain, and less prone to errors.
- Example: If you want to ensure that only users with an “active” account status can use any part of your API, you can put this check in an authorization filter. This way, every endpoint is automatically protected, and you don’t have to repeat the check in each controller.
Custom Authorization Rules
Sometimes your access rules aren’t just about simple roles—they might depend on complex business logic (e.g., time-based access, department-specific rules, or dynamic permissions). Authorization filters let you implement any custom logic you need.
- Example: In a financial trading platform API, only users who have completed a KYC (Know Your Customer) verification can place trades. Or, certain actions (like high-value transfers) are only allowed during business hours, enforced via custom logic in an authorization filter.
Securing APIs Exposed to Third Parties
If your API is open to third-party apps or partners, you must ensure that only trusted, authorized partners can access certain endpoints or data.
- Example: A payment processing API might allow only registered and approved merchants (not regular users) to access endpoints for issuing refunds or generating financial reports.
Authorization filters in ASP.NET Core Web API provide a robust, flexible, and declarative way to enforce security at the API level. By using built-in attributes such as [Authorize] and [AllowAnonymous], developers can easily control access to controllers and actions based on user authentication and roles. This ensures that only properly authenticated and authorized users can access sensitive endpoints, reducing the risk of unauthorized data exposure and misuse. Whether implementing simple role-based restrictions or more advanced policies, authorization filters help centralize and simplify security management.
In the next article, I will discuss how to Create Custom Authorization Filters in ASP.NET Core Web API Applications with Examples. In this article, I explain Authorization Filters in ASP.NET Core Web API Applications. I hope you enjoy this article on Authorization Filters in ASP.NET Core Web API.
