Back to: ASP.NET Core Identity Tutorials
Custom Password Policy in ASP.NET Core Identity
In this article, I will discuss How to Implement a Custom Password Policy in ASP.NET Core Identity with Examples. Please read our previous article discussing Login and Logout Functionalities in ASP.NET Core Identity. Before customizing the Password Policy in ASP.NET Core Identity, let us first understand the default Password Policy in ASP.NET Core Identity.
ASP.NET Core Identity Default Password Policy
ASP.NET Core Identity has a default Password Policy designed to enhance the security of your application. The Password Policy in ASP.NET Core Identity is implemented by the PasswordOptions class, and if you go to the definition of this class, you will see the following:
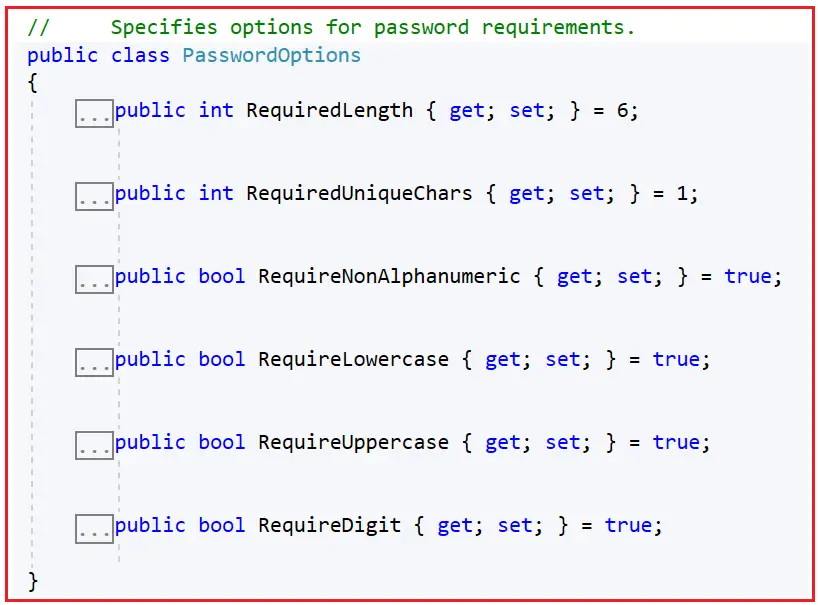
This default policy includes the following rules:
- Required Length: Passwords must be at least 6 characters long.
- Require Digit: The password requires at least one numeric digit (‘0’-‘9’). The default is true.
- Require Lowercase: The password must contain at least one lowercase character (‘a’-‘z’). The default is true.
- Require Uppercase: The password must include at least one uppercase character (‘A’-‘Z’). The default is true.
- Require Non-Alphanumeric: The password requires at least one non-alphanumeric character (e.g., symbols like ‘!’, ‘@’, ‘#’). The default is true.
- Required Unique Chars: The number of distinct characters must be in the password. The default is 1.
These settings ensure that the application’s passwords are relatively strong, helping to protect user accounts from common attacks such as Brute Force.
What is a Brute Force Attack?
A Brute Force Attack is a method of cracking a password by systematically trying every possible combination until the correct one is found. This approach is straightforward and doesn’t exploit any technical vulnerability in the encryption or authentication mechanism; rather, it relies on computing power to try all conceivable options.
To verify the default password policy, run the application and register a new user using password 1234, and you will see the following error messages showing the default password policy.

Customizing ASP.NET Core Identity Password Policy
Implementing a custom password policy in ASP.NET Core Identity is a great way to enhance the security of your applications by enforcing specific password rules that users must follow. Strong Password Policies help protect user accounts from common threats like brute-force attacks. Now, we want the following in our Password Policy:
- The password must be at least 8 characters long.
- It must contain digits, both uppercase and lowercase letters, and non-alphanumeric characters.
- It requires at least four unique characters.
As we already seen the PasswordOptions class contains settings like required length, required unique chars, and requirements for non-alphanumeric, lowercase, uppercase, and numeric characters. To configure the Custom Password Policy in ASP.NET Core Identity, we need to modify the Settings in the Program.cs file. So, modify the Identity Settings as follows within the Program.cs class file:
//Configuration Identity Services
builder.Services.AddIdentity<IdentityUser, IdentityRole>(
options =>
{
// Password settings
options.Password.RequireDigit = true;
options.Password.RequiredLength = 8;
options.Password.RequireNonAlphanumeric = true;
options.Password.RequireUppercase = true;
options.Password.RequireLowercase = true;
options.Password.RequiredUniqueChars = 4;
// Other settings can be configured here
})
.AddEntityFrameworkStores<ApplicationDbContext>();
With the above changes in place, run the application and verify whether the custom password policy is working as expected. Provide the password as 1122 and see what error messages you get.

Now, provide a valid password that follows the password policy, and the user should be created. Let us provide the password as Abcd@#1234, as shown in the image below.

Once you click on the Register button, the user must be created, and you can check the same in the database, as shown in the image below. It should show the newly added user. ASP.NET Core Identity uses a password hashing algorithm based on the HMACSHA256 algorithm.

When to Implement a Custom Password Policy in ASP.NET Core Identity?
Implementing a custom password policy in ASP.NET Core Identity is used for enhancing security, complying with regulatory standards, and adapting to specific business requirements. The following are some scenarios where we need to consider implementing a custom password policy:
- Enhanced Security Requirements: If your application handles sensitive data, such as financial information or personal information, you might require stronger password policies than the default settings to increase security.
- Compliance with Standards and Regulations: Different industries have regulations that specify minimum security standards, including password policies. For instance, healthcare applications in the U.S. might need to comply with HIPAA, while payment applications might need to adhere to PCI DSS standards.
- Specific Business Needs: Depending on the nature of your business, you may want to implement specific rules that are not covered by ASP.NET Core Identity’s default password validators. For example, you might want to prevent the use of commonly used passwords or enforce password changes after a certain period.
In the next article, I will discuss How to Redirect to ReturnUrl After Login in ASP.NET Core Identity. In this article, I try to explain how to implement a Custom Password Policy in ASP.NET Core Identity. I hope you enjoy this article, “How to Implement Custom Password Policy in ASP.NET Core Identity.”
