Back to: AWS Tutorials For Beginners and Professionals
Security Groups and Classic Ports in AWS
In this article, I will overview Security Groups and Classic Ports in AWS. Please read our previous article discussing AWS EC2 Instance Types with Examples.
Security Groups and Classic Ports in AWS
Security groups act as virtual firewalls that control traffic to and from your EC2 instances. They are essential for managing network security in the AWS cloud.
- Allow Rules Only: Security groups only allow you to define what traffic is permitted. You cannot create deny rules. If traffic is not explicitly allowed, it is implicitly denied.
- Inbound and Outbound Traffic:
- Inbound Rules: Control the traffic that is allowed to enter the EC2 instance.
- Outbound Rules: Control the traffic that is allowed to leave the EC2 instance.
- Referencing:
- By IP Address: You can specify which IP addresses are allowed to communicate with your EC2 instance.
- By Other Security Groups: Security groups can reference each other. This is useful when you have multiple EC2 instances that need to communicate securely within the AWS environment.
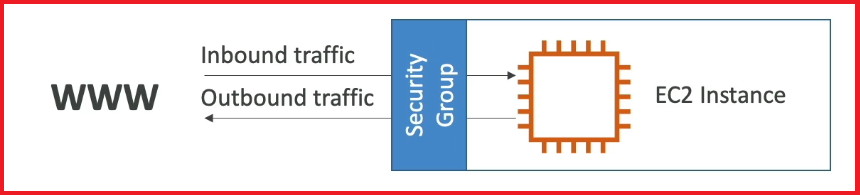
Imagine you’re trying to access your EC2 instance from your computer, which is on the public internet. You would set up a security group around your EC2 instance that specifies:
- Inbound Rules: Which IP addresses (e.g., your computer’s IP) can access the instance and on which ports (e.g., port 22 for SSH).
- Outbound Rules: Whether the EC2 instance can initiate outbound traffic to the internet or other instances.
Let’s explore the specifics of security groups and how they function as firewalls for your EC2 instances.
Key Components of Security Group Rules:
Type: Specifies the type of traffic (e.g., SSH, HTTP, HTTPS) that is being controlled. The type defines what kind of service or application the rule applies to.
Protocol: This defines the communication protocol, such as TCP or UDP, that determines how data is transmitted over the network.
Port Range: Specifies which ports on the EC2 instance are open for traffic. For example, port 22 is typically used for SSH, while port 80 is used for HTTP traffic.
Source (for Inbound Rules) / Destination (for Outbound Rules):
Source: Defines where the incoming traffic is coming from. This can be an IP address range. For example:
0.0.0.0/0: This notation means “any IP address,” allowing traffic from anywhere on the internet.
192.168.1.1/32: This specifies a single IP address, allowing traffic only from that specific address.
Destination: In the case of outbound rules, this defines where the outgoing traffic is allowed to go.
IP Versions: IPv4 and IPv6: Security groups support both IPv4 (most commonly used) and IPv6 (newer and more expanded) addresses. When creating rules, you can specify whether they apply to IPv4, IPv6, or both.
Inbound and Outbound Control:
Inbound Network Control: Manages traffic coming into the EC2 instance. For example, you might allow SSH traffic (port 22) only from a specific IP address.
Outbound Network Control: Manages traffic leaving the EC2 instance. For instance, you might allow the instance to access the internet on port 80 for HTTP requests.
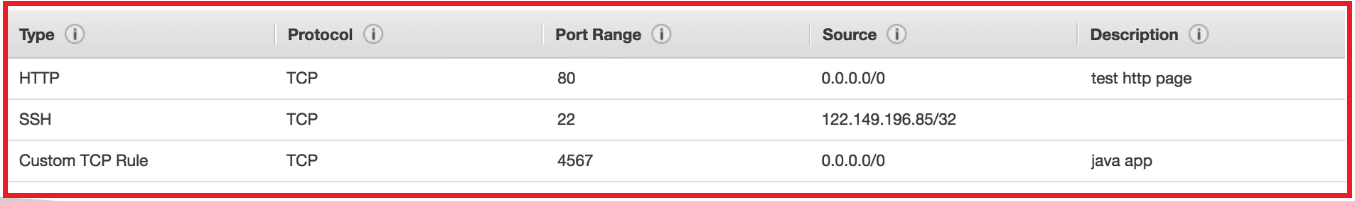
Example Rule:
A typical security group rule might look like this:
- Type: SSH
- Protocol: TCP
- Port Range: 22
- Source: 0.0.0.0/0 (allowing SSH access from any IP address)
Security Group Setup in AWS:
- Inbound Rules: Control traffic coming into the EC2 instance. For example, if you set up an inbound rule on port 22 (used for SSH), only computers with the authorized IP address can connect to your EC2 instance via SSH. If someone else’s computer tries to connect without the correct IP, the security group will block the attempt, and they’ll experience a timeout.
- Outbound Rules: Control traffic leaving the EC2 instance. By default, outbound rules in AWS security groups allow all traffic to go out. This means that your EC2 instance can access the internet or other services without restrictions.

Practical Example:
- Inbound: With the authorized IP, your computer can SSH into the EC2 instance on port 22. However, an unauthorized computer with a different IP address won’t be able to connect because the security group will block the traffic.
- Outbound: Your EC2 instance can freely initiate outbound connections, such as website access because the default outbound rules allow all traffic out.
This is how the security group acts as a firewall around your EC2 instance: it controls who can access the instance from the outside and allows the instance to communicate with the outside world.
Key Features of Security Groups:
- Multiple Attachments:
- Security groups can be attached to multiple EC2 instances, and a single EC2 instance can have multiple security groups.
- This flexibility allows you to manage access control across various instances efficiently.
- Region/VPC-Specific:
- Security groups and Virtual Private Cloud (VPC) are specific to a particular region. If you switch regions or create a new VPC, you must create new security groups in that context.
- External Firewall:
- Security groups operate outside of the EC2 instance. If a security group blocks traffic, the instance never sees it. This differs from application-level firewalls, as security groups work at the network level.
- Best Practices for SSH:
- It’s recommended that a dedicated security group be established for SSH access. This helps ensure that your SSH settings are correct and secure without interference from other rules.
- Troubleshooting Connections:
- If you experience a timeout when connecting to your EC2 instance, it’s likely a security group issue (i.e., the traffic is blocked).
- If you receive a “connection refused” error, the traffic is getting through, but the application on the EC2 instance is not responding, possibly because it’s not running or configured correctly.
- Default Rules:
- By default, all inbound traffic is blocked, and all outbound traffic is allowed. This default setup ensures your instance is secure by not accepting unsolicited incoming connections unless explicitly allowed.

Advanced Feature: Security Group Referencing
- Referencing Other Security Groups:
- You can set up security groups to reference other security groups. This means that instead of specifying IP addresses, you allow traffic from any instance that has a specific security group attached.
- This is particularly useful when dealing with load balancers or when you have instances that need to communicate with each other without worrying about specific IP addresses.
Example Scenario:
- Group 1 and Group 2:
- If EC2 instance A has Security Group 1 attached and allows inbound traffic from Security Group 2, then any instance with Security Group 2 (say instance B) can communicate with instance A.
- This dynamic setup doesn’t require you to manage IP addresses, making it easier to manage communications between instances.
Let’s summarize the key ports you need to know when working with EC2 instances and security groups in AWS:
Essential Ports:
- Port 22 (SSH – Secure Shell):
- Purpose: Used for securely logging into a Linux EC2 instance.
- Use Case: Allows you to access and manage a Linux server remotely.
- Port 21 (FTP – File Transfer Protocol):
- Purpose: Used for transferring files to and from a server.
- Use Case: Commonly used to upload files to a file share, though less secure than other methods.
- Port 22 (SFTP – Secure File Transfer Protocol):
- Purpose: Similar to FTP but more secure because it uses SSH for encryption.
- Use Case: Securely transferring files to and from a server over SSH.
- Port 80 (HTTP – Hypertext Transfer Protocol):
- Purpose: Used for accessing unsecured websites.
- Use Case: Browsing the web without encryption (less common nowadays).
- Port 443 (HTTPS – Hypertext Transfer Protocol Secure):
- Purpose: Used for accessing secured websites.
- Use Case: Browsing the web with encryption, ensuring secure data transmission (standard for most websites today).
- Port 3389 (RDP – Remote Desktop Protocol):
- Purpose: Used for logging into a Windows EC2 instance.
- Use Case: Allows remote access to a Windows server, similar to SSH for Linux but for Windows environments.
These are the essential ports you need to be familiar with when configuring security groups in AWS:
- Port 22 for SSH and SFTP (Linux)
- Port 21 for FTP
- Port 80 for HTTP
- Port 443 for HTTPS
- Port 3389 for RDP (Windows)
Understanding these ports helps you effectively manage access to your EC2 instances, ensuring the correct protocols are allowed for the right services.
In the next article, I will discuss Security Groups and Classic Ports in AWS. In this article, I explain Security Groups and Classic Ports in AWS. I hope you enjoy this article.
Registration Open – Mastering Design Patterns, Principles, and Architectures using .NET
Session Time: 6:30 AM – 08:00 AM IST
Advance your career with our expert-led, hands-on live training program. Get complete course details, the syllabus, and Zoom credentials for demo sessions via the links below.
- View Course Details & Get Demo Credentials
- Registration Form
- Join Telegram Group
- Join WhatsApp Group
