Back to: ASP.NET Core Identity Tutorials
Policy-Based Authorization in ASP.NET Core Identity
In this article, I will discuss how to implement Policy-Based Authorization in ASP.NET Core Identity. Please read our previous article discussing Claims-Based Authorization in ASP.NET Core Identity.
Authorization is a critical part of any application that determines what a user is allowed to do. While claims-based authorization directly checks for specific claims on the user, ASP.NET Core provides a more flexible mechanism called policy-based authorization. This approach enables developers to define reusable authorization policies and apply them declaratively in controllers or views.
What is Policy-Based Authorization?
Policy-based authorization is an approach where access control rules are encapsulated into policies. Each policy is defined with one or more requirements, and each requirement is evaluated against the user’s claims. If all requirements in a policy are satisfied, access is granted.
A policy is essentially a named rule that we can configure once and reuse across our application. This avoids repetitive inline claim checks inside controllers and views, making our code cleaner and more maintainable.
Why Do We Need to Use Policy-Based Authorization?
While claims-based authorization answers the question “Does this user have a particular claim?”, policy-based authorization goes one step further by grouping one or more claim requirements into a logical policy.
For example:
- Claim-based approach → User.HasClaim(“Permission”, ” EditUser”) within the action method body.
- Policy-based approach → [Authorize(Policy=”EditUserPolicy”)]
With policies:
- The rules are centrally managed in the Program.cs class file.
- You can enforce complex conditions (multiple claims, roles, or custom requirements).
- Changes are applied globally without modifying individual controllers.
How Policy-Based Authorization Works in ASP.NET Core Identity?
Let us understand this step by step. To better understand How Policy-Based Authorization Works in ASP.NET Core Identity, please have a look at the following image.
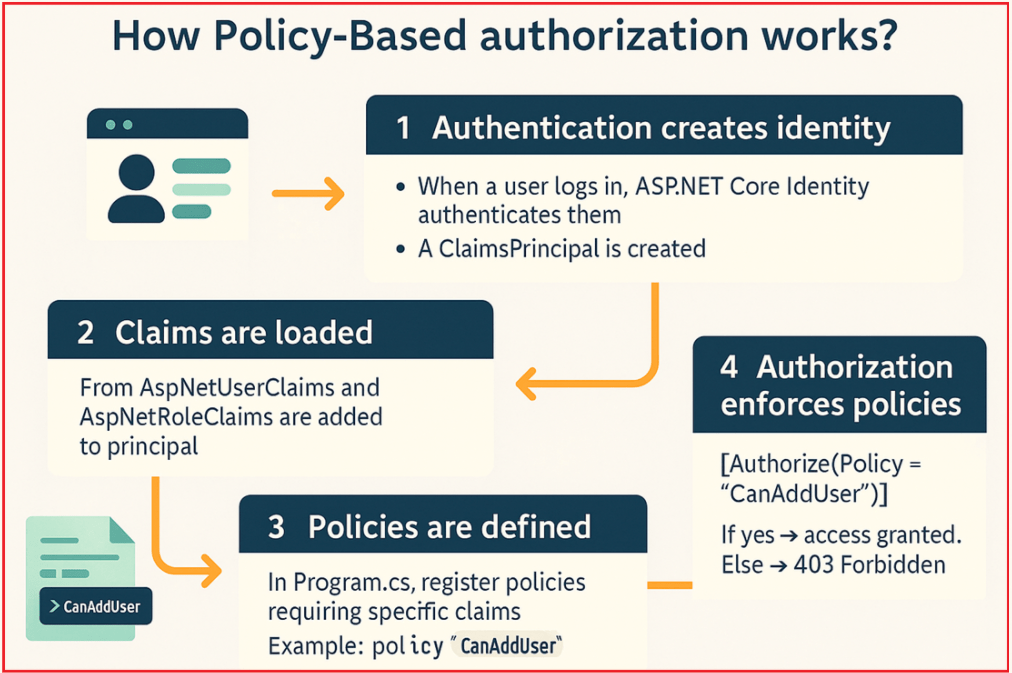
Authentication creates identity
- When a user logs in, ASP.NET Core Identity authenticates them.
- A ClaimsPrincipal object is created with both user claims and role claims.
Claims are loaded
- User-specific claims come from the AspNetUserClaims table.
- Role claims come from the AspNetRoleClaims table.
- Both are added to the user’s principal.
Policies are defined
- In Program.cs class, we register policies that require specific claims.
- Example: A policy named “CanAddUser” requires a claim (Permission, AddUser).
Authorization Enforces Policies
- When a controller or Razor page is decorated with [Authorize(Policy = “CanAddUser”)], ASP.NET Core checks if the user’s claims satisfy that policy.
- If yes → access granted. If not → 403 Forbidden.
Define Policies in Program.cs:
Please add the following code to the Program class file.
//Defining Policies
builder.Services.AddAuthorization(options =>
{
// ========= Single-claim policies (one claim is enough) =========
options.AddPolicy("AddUserPolicy", policy =>
policy.RequireClaim("Permission", "AddUser"));
options.AddPolicy("EditUserPolicy", policy =>
policy.RequireClaim("Permission", "EditUser"));
options.AddPolicy("DeleteUserPolicy", policy =>
policy.RequireClaim("Permission", "DeleteUser"));
options.AddPolicy("ViewUsersPolicy", policy =>
policy.RequireClaim("Permission", "ViewUsers"));
// ========= Multiple OR claims (any one is enough) =========
// Access if user has either EditUser OR ManageUsers
options.AddPolicy("ManageUsersPolicy", policy =>
policy.RequireAssertion(ctx =>
ctx.User.HasClaim("Permission", "EditUser") ||
ctx.User.HasClaim("Permission", "ManageUsers")));
// ========= Multiple AND claims (all required) =========
// To manage roles on a user, require full role-permission set
// (useful when AddRole/EditRole/DeleteRole are distinct permissions)
options.AddPolicy("ManageRolesPolicy", policy =>
policy.RequireAssertion(ctx =>
ctx.User.HasClaim("Permission", "AddRole") &&
ctx.User.HasClaim("Permission", "EditRole") &&
ctx.User.HasClaim("Permission", "DeleteRole")));
});
Single-Claim Policies
These are straightforward checks where one claim grants access. Protect actions that require one specific permission. For example:
- “AddUserPolicy” → only users with the claim (Permission=AddUser) can create users.
- “EditUserPolicy” → only users with the claim (Permission=EditUser) can edit users.
- “DeleteUserPolicy” → only users with the claim (Permission=DeleteUser) can delete users.
- “ViewUsersPolicy” → only users with the claim (Permission=ViewUsers) can view user details.
Multiple OR Claims Policies
This pattern is useful when different roles or claim-sets can unlock the same functionality. It allows access if the user satisfies any one of several conditions. For example:
- “ManageUsersPolicy” → the user can manage users if they have either (Permission=EditUser) OR (Permission=ManageUsers).
Multiple AND Claims Policies
This ensures only users with a complete set of permissions can perform critical operations like role management. It requires the user to have a combination of claims simultaneously. For example:
- “ManageRolesPolicy” → the user must have all three claims (Permission=AddRole, EditRole, DeleteRole) before they are allowed to manage roles.
Applying Policies in Controller:
Once we have defined policies in the Program class file using AddAuthorization(options => {…}), we can then enforce those policies inside controllers/actions by applying the [Authorize] attribute with the Policy property.
Syntax: [Authorize(Policy = “PolicyName”)]
Here,
- PolicyName → should match the exact string you configured in your AddAuthorization setup.
- You can apply the policy at:
- Controller level → applies to all actions inside the controller.
- Action level → applies only to that specific method.
Apply Different Policies in the Controller. Please modify the Users Controller as follows:
using ASPNETCoreIdentityDemo.Services;
using ASPNETCoreIdentityDemo.ViewModels;
using ASPNETCoreIdentityDemo.ViewModels.Users;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Identity;
using Microsoft.AspNetCore.Mvc;
using Microsoft.EntityFrameworkCore;
namespace ASPNETCoreIdentityDemo.Controllers
{
// Require authentication for ALL actions in this controller
[Authorize]
public class UsersController : Controller
{
private readonly IUserService _userService;
private readonly ILogger<UsersController> _logger;
public UsersController(IUserService userService, ILogger<UsersController> logger)
{
_userService = userService;
_logger = logger;
}
// GET: /Users
[HttpGet]
[Authorize(Policy = "ViewUsersPolicy")]
public async Task<IActionResult> Index([FromQuery] UserListFilterViewModel filter)
{
try
{
var result = await _userService.GetUsersAsync(filter);
ViewBag.Filter = filter;
return View(result);
}
catch (Exception ex)
{
_logger.LogError(ex, "Error loading users list.");
SetError("We couldn’t load the users right now. Please try again.");
return View(new PagedResult<UserListItemViewModel>());
}
}
// GET: /Users/Create
[HttpGet]
[Authorize(Policy = "AddUserPolicy")]
public IActionResult Create()
{
return View(new UserCreateViewModel());
}
// POST: /Users/Create
[HttpPost]
[Authorize(Policy = "AddUserPolicy")]
[ValidateAntiForgeryToken]
public async Task<IActionResult> Create(UserCreateViewModel model)
{
try
{
if (!ModelState.IsValid)
return View(model);
var (result, newId) = await _userService.CreateAsync(model);
if (result.Succeeded)
{
SetSuccess($"User '{model.Email}' was created successfully.");
return RedirectToAction(nameof(Index));
}
AddIdentityErrors(result);
return View(model);
}
catch (DbUpdateException dbx)
{
_logger.LogError(dbx, $"DB error while creating user {model.Email}");
SetError("We couldn’t create the user due to a database error. Please try again.");
return View(model);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Unexpected error creating user {model.Email}");
SetError("An unexpected error occurred while creating the user.");
return View(model);
}
}
// GET: /Users/Edit/{id}
[HttpGet]
[Authorize(Policy = "EditUserPolicy")]
public async Task<IActionResult> Edit(Guid id)
{
try
{
var userEditViewModel = await _userService.GetForEditAsync(id);
if (userEditViewModel == null)
{
SetError("The user you’re trying to edit was not found.");
return RedirectToAction(nameof(Index));
}
return View(userEditViewModel);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Error loading edit form for user {id}");
SetError("We couldn’t load the edit form. Please try again.");
return RedirectToAction(nameof(Index));
}
}
// POST: /Users/Edit
[HttpPost]
[Authorize(Policy = "EditUserPolicy")]
[ValidateAntiForgeryToken]
public async Task<IActionResult> Edit(UserEditViewModel model)
{
try
{
if (!ModelState.IsValid)
return View(model);
var result = await _userService.UpdateAsync(model);
if (result.Succeeded)
{
SetSuccess("User was updated successfully.");
return RedirectToAction(nameof(Index));
}
if (result.Errors.Any(e =>
string.Equals(e.Code, "ConcurrencyFailure", StringComparison.OrdinalIgnoreCase)))
{
SetError("This user was modified by another admin. Please reload the page and try again.");
}
AddIdentityErrors(result);
return View(model);
}
catch (DbUpdateConcurrencyException cex)
{
_logger.LogWarning(cex, $"Concurrency error updating user {model.Id}");
SetError("Your changes could not be saved because another update occurred. Please reload and try again.");
return View(model);
}
catch (DbUpdateException dbx)
{
_logger.LogError(dbx, $"DB error while updating user {model.Id}");
SetError("We couldn’t update the user due to a database error. Please try again.");
return View(model);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Unexpected error updating user {model.Id}");
SetError("An unexpected error occurred while updating the user.");
return View(model);
}
}
// GET: /Users/Details/{id}
[HttpGet]
[Authorize(Policy = "ViewUsersPolicy")]
public async Task<IActionResult> Details(Guid id)
{
try
{
var userDetailsViewModel = await _userService.GetDetailsAsync(id);
if (userDetailsViewModel == null)
{
SetError("The requested user was not found.");
return RedirectToAction(nameof(Index));
}
return View(userDetailsViewModel);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Error loading details for user {id}");
SetError("We couldn’t load the user details. Please try again.");
return RedirectToAction(nameof(Index));
}
}
// GET: /Users/Delete/{id}
[HttpGet]
[Authorize(Policy = "DeleteUserPolicy")]
public async Task<IActionResult> Delete(Guid id)
{
try
{
var userDetailsViewModel = await _userService.GetDetailsAsync(id);
if (userDetailsViewModel == null)
{
SetError("The user you’re trying to delete was not found.");
return RedirectToAction(nameof(Index));
}
return View(userDetailsViewModel);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Error loading delete confirmation for user {id}");
SetError("We couldn’t load the delete confirmation. Please try again.");
return RedirectToAction(nameof(Index));
}
}
// POST: /Users/DeleteConfirmed
[HttpPost]
[Authorize(Policy = "DeleteUserPolicy")]
[ValidateAntiForgeryToken]
public async Task<IActionResult> DeleteConfirmed(Guid id)
{
if (id == Guid.Empty) return NotFound();
try
{
var result = await _userService.DeleteAsync(id);
if (result.Succeeded)
{
SetSuccess("User was deleted successfully.");
return RedirectToAction(nameof(Index));
}
if (result.Errors.Any(e => string.Equals(e.Code, "LastAdmin", StringComparison.OrdinalIgnoreCase)))
{
SetError("You cannot delete the last user in the ‘Admin’ role.");
}
else if (result.Errors.Any(e => string.Equals(e.Code, "NotFound", StringComparison.OrdinalIgnoreCase)))
{
SetError("The user no longer exists.");
}
else
{
SetError(string.Join(" ", result.Errors.Select(e => e.Description)));
}
return RedirectToAction(nameof(Index));
}
catch (DbUpdateException dbx)
{
_logger.LogError(dbx, $"DB error while deleting user {id}");
SetError("We couldn’t delete the user due to a database error. Please try again.");
return RedirectToAction(nameof(Index));
}
catch (Exception ex)
{
_logger.LogError(ex, $"Unexpected error deleting user {id}");
SetError("An unexpected error occurred while deleting the user.");
return RedirectToAction(nameof(Index));
}
}
// GET: /Users/ManageRoles/{id}
[HttpGet]
[Authorize(Policy = "ManageRolesPolicy")] // all Add/Edit/DeleteRole required
public async Task<IActionResult> ManageRoles(Guid id)
{
try
{
var userRolesEditViewModel = await _userService.GetRolesForEditAsync(id);
if (userRolesEditViewModel == null)
{
SetError("The user was not found.");
return RedirectToAction(nameof(Index));
}
return View(userRolesEditViewModel);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Error loading roles editor for user {id}");
SetError("We couldn’t load the roles editor. Please try again.");
return RedirectToAction(nameof(Index));
}
}
// POST: /Users/ManageRoles
[HttpPost, ValidateAntiForgeryToken]
[Authorize(Policy = "ManageRolesPolicy")]
public async Task<IActionResult> ManageRoles(UserRolesEditViewModel model)
{
if (!ModelState.IsValid)
return View(model);
try
{
var selected = model.Roles.Where(r => r.IsSelected).Select(r => r.RoleId).ToList();
var result = await _userService.UpdateRolesAsync(model.UserId, selected);
if (result.Succeeded)
{
SetSuccess("User roles were updated successfully.");
return RedirectToAction(nameof(Details), new { id = model.UserId });
}
if (result.Errors.Any(e => string.Equals(e.Code, "RoleNotFound", StringComparison.OrdinalIgnoreCase)))
{
SetError("One or more selected roles no longer exist. Please refresh and try again.");
}
AddIdentityErrors(result);
var userRolesEditViewModel = await _userService.GetRolesForEditAsync(model.UserId);
return View(userRolesEditViewModel ?? model);
}
catch (DbUpdateException dbx)
{
_logger.LogError(dbx, $"DB error while updating roles for user {model.UserId}");
SetError("We couldn’t update roles due to a database error. Please try again.");
var vm = await _userService.GetRolesForEditAsync(model.UserId);
return View(vm ?? model);
}
catch (Exception ex)
{
_logger.LogError(ex, $"Unexpected error updating roles for user {model.UserId}");
SetError("An unexpected error occurred while updating roles.");
var vm = await _userService.GetRolesForEditAsync(model.UserId);
return View(vm ?? model);
}
}
// GET: /Users/ManageClaims/{id} - Admin only
[Authorize(Roles = "Admin")]
[HttpGet]
public async Task<IActionResult> ManageClaims(Guid id)
{
var userClaimsEditViewModel = await _userService.GetClaimsForEditAsync(id);
if (userClaimsEditViewModel == null)
{
SetError("The user was not found.");
return RedirectToAction(nameof(Index));
}
return View(userClaimsEditViewModel);
}
// POST: /Users/ManageClaims - Admin only
[Authorize(Roles = "Admin")]
[HttpPost, ValidateAntiForgeryToken]
public async Task<IActionResult> ManageClaims(UserClaimsEditViewModel model)
{
if (!ModelState.IsValid)
return View(model);
try
{
var selected = model.Claims.Where(c => c.IsSelected).Select(c => c.ClaimId).ToList();
var result = await _userService.UpdateClaimsAsync(model.UserId, selected);
if (result.Succeeded)
{
SetSuccess("User claims were updated successfully.");
return RedirectToAction(nameof(Details), new { id = model.UserId });
}
if (result.Errors.Any(e => string.Equals(e.Code, "InvalidClaimSelection", StringComparison.OrdinalIgnoreCase)))
SetError("One or more selected claims are not assignable to users. Please refresh and try again.");
AddIdentityErrors(result);
var reload = await _userService.GetClaimsForEditAsync(model.UserId);
return View(reload ?? model);
}
catch (DbUpdateException dbx)
{
_logger.LogError(dbx, "DB error while updating claims for user {UserId}", model.UserId);
SetError("We couldn’t update claims due to a database error. Please try again.");
var reload = await _userService.GetClaimsForEditAsync(model.UserId);
return View(reload ?? model);
}
catch (Exception ex)
{
_logger.LogError(ex, "Unexpected error updating claims for user {UserId}", model.UserId);
SetError("An unexpected error occurred while updating claims.");
var reload = await _userService.GetClaimsForEditAsync(model.UserId);
return View(reload ?? model);
}
}
#region Helpers
// Helper: Push a success message into TempData (survives redirect)
private void SetSuccess(string message)
{
TempData["Success"] = message;
}
// Helper: Push an error message into TempData (survives redirect)
private void SetError(string message)
{
TempData["Error"] = message;
}
// Helper: Copy IdentityResult errors into ModelState
// so they can be displayed by validation summary in views.
private void AddIdentityErrors(IdentityResult result)
{
if (result == null || result.Succeeded) return;
foreach (var e in result.Errors)
ModelState.AddModelError(string.Empty, e.Description);
}
#endregion
}
}
Applying Policies in View:
In ASP.NET Core, the policies can be enforced not only in controllers and actions, but also in Razor views. This allows us to dynamically show or hide parts of the UI depending on whether the logged-in user meets the authorization requirements.
How to Use Policies in Vies:
- First, you need to inject the IAuthorizationService into your view using @inject. The IAuthorizationService service belongs to Microsoft.AspNetCore.Authorization namespace.
- Then call AuthorizeAsync(User, “PolicyName”) to check if the logged-in user satisfies the policy.
- This gives more control (e.g., assigning the result to a variable, combining multiple checks, showing/hiding sections of UI).
Syntax:
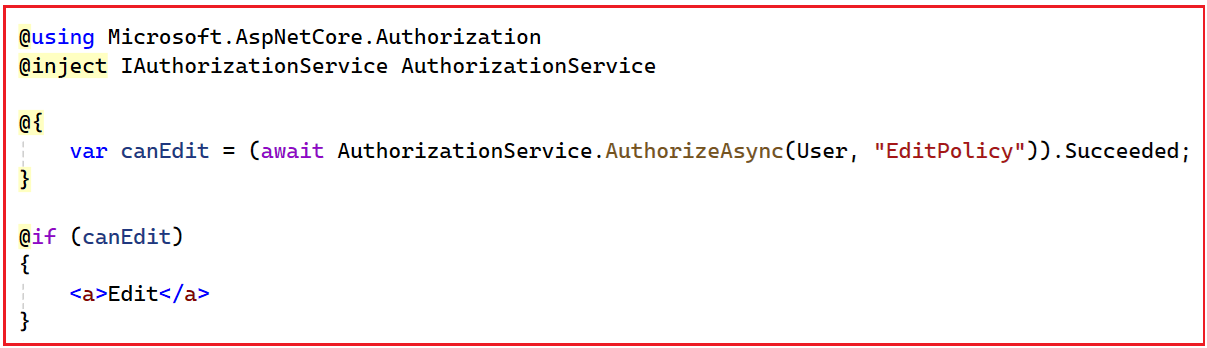
Using policies in Razor Views ensures the UI and the backend speak the same authorization language, giving users only what they’re allowed to see and do, while keeping security centralized and consistent. So, please modify the Index View of Users Controller as follows:
@using Microsoft.AspNetCore.Authorization
@inject IAuthorizationService AuthorizationService
@using ASPNETCoreIdentityDemo.ViewModels
@using ASPNETCoreIdentityDemo.ViewModels.Users
@model PagedResult<UserListItemViewModel>
@{
ViewData["Title"] = "Users";
var filter = (UserListFilterViewModel)ViewBag.Filter;
var canCreateUser = (await AuthorizationService.AuthorizeAsync(User, "AddUserPolicy")).Succeeded;
var canEditUser = (await AuthorizationService.AuthorizeAsync(User, "EditUserPolicy")).Succeeded;
var canDeleteUser = (await AuthorizationService.AuthorizeAsync(User, "DeleteUserPolicy")).Succeeded;
var canViewDetails = (await AuthorizationService.AuthorizeAsync(User, "ViewUsersPolicy")).Succeeded;
var canManageRoles = (await AuthorizationService.AuthorizeAsync(User, "ManageRolesPolicy")).Succeeded;
// Special case: Manage Claims remains role-based (Admin only, for testing)
bool canManageClaims = User?.IsInRole("Admin") ?? false;
bool showActionsCol = canViewDetails || canEditUser || canManageRoles || canDeleteUser;
}
@if (User?.HasClaim("Permission", "ViewUsers") ?? false)
{
<a asp-action="Details">View Users</a>
}
<div class="container mt-1">
<div class="d-flex flex-wrap align-items-center justify-content-between gap-2 mb-4 pb-2 border-bottom">
<div>
<h1 class="h3 mb-1 fw-bold text-primary">Users Administration</h1>
<p class="text-muted mb-0">Search, filter, and manage application users.</p>
</div>
@* Create User: Allowed only if user has pass the AddUserPolicy *@
@if (canCreateUser)
{
<div>
<a asp-action="Create" class="btn btn-primary">
<i class="bi bi-plus-lg me-1"></i> Add New User
</a>
</div>
}
</div>
@if (TempData["Success"] is string sMsg)
{
<div class="alert alert-success alert-dismissible fade show" role="alert">
<i class="bi bi-check-circle me-2"></i>@sMsg
<button type="button" class="btn-close" data-bs-dismiss="alert" aria-label="Close"></button>
</div>
}
@if (TempData["Error"] is string eMsg)
{
<div class="alert alert-danger alert-dismissible fade show" role="alert">
<i class="bi bi-exclamation-triangle me-2"></i>@eMsg
<button type="button" class="btn-close" data-bs-dismiss="alert" aria-label="Close"></button>
</div>
}
<!-- Filter Bar -->
<form method="get" class="row g-2 align-items-end mb-3">
<div class="col-md-4">
<label class="form-label">Search</label>
<input name="Search" value="@filter.Search" class="form-control"
placeholder="Search name, email, phone, username" />
</div>
<div class="col-md-2">
<label class="form-label">Status</label>
<select name="IsActive" class="form-select">
<option value="">All Status</option>
<option value="true" selected="@(filter.IsActive == true)">Active</option>
<option value="false" selected="@(filter.IsActive == false)">Inactive</option>
</select>
</div>
<div class="col-md-2">
<label class="form-label">Email</label>
<select name="EmailConfirmed" class="form-select">
<option value="">All Emails</option>
<option value="true" selected="@(filter.EmailConfirmed == true)">Confirmed</option>
<option value="false" selected="@(filter.EmailConfirmed == false)">Unconfirmed</option>
</select>
</div>
<div class="col-md-2">
<label class="form-label">Page Size</label>
<select name="PageSize" class="form-select">
@foreach (var size in new[] { 5, 10, 20, 50 })
{
<option value="@size" selected="@(filter.PageSize == size)">@size / page</option>
}
</select>
</div>
<div class="col-md-2 d-grid d-sm-flex gap-2">
<button class="btn btn-primary" type="submit">
<i class="bi bi-funnel me-1"></i> Apply
</button>
<!-- Clear = go to Index without query string -->
<a asp-action="Index" class="btn btn-info">
<i class="bi bi-x-circle me-1"></i> Clear
</a>
</div>
</form>
<div class="card shadow border-0 rounded">
<div class="card-body p-0">
<div class="table-responsive">
<table class="table align-middle mb-0">
<thead class="table-dark">
<tr>
<th>Name</th>
<th>Email</th>
<th>Phone</th>
<th>Status</th>
<th>Email Status</th>
<th>Created</th>
@if (showActionsCol)
{
<th class="text-end">Actions</th>
}
</tr>
</thead>
<tbody>
@if (!Model.Items.Any())
{
<tr>
<td colspan="@(showActionsCol ? 7 : 6)" class="text-center text-muted py-4">No users found.</td>
</tr>
}
else
{
foreach (var u in Model.Items)
{
<tr>
<td>@($"{u.FirstName} {u.LastName}".Trim())</td>
<td>@u.Email</td>
<td>@u.PhoneNumber</td>
<td>
@if (u.IsActive)
{
<span class="badge rounded-pill bg-success">Active</span>
}
else
{
<span class="badge rounded-pill bg-danger">Inactive</span>
}
</td>
<td>
@if (u.EmailConfirmed)
{
<span class="badge rounded-pill bg-success">Confirmed</span>
}
else
{
<span class="badge rounded-pill bg-warning text-dark">Unconfirmed</span>
}
</td>
<td>@u.CreatedOn?.ToString("yyyy-MM-dd")</td>
@if (showActionsCol)
{
<td class="text-end">
@*
Show "Details" button only if user passes ViewUsersPolicy
(requires Permission = "ViewUsers").
This ensures that only authorized users can view user profiles.
*@
@if (canViewDetails)
{
<a asp-action="Details" asp-route-id="@u.Id" class="btn btn-sm btn-outline-info me-1">
<i class="bi bi-card-list me-1"></i> Details
</a>
}
@*
Show "Edit" button only if user passes EditUserPolicy
(requires Permission = "EditUser").
Prevents unauthorized users from modifying user data.
*@
@if (canEditUser)
{
<a asp-action="Edit" asp-route-id="@u.Id" class="btn btn-sm btn-outline-primary me-1">
<i class="bi bi-pencil-square me-1"></i> Edit
</a>
}
@*
Show "Manage Claims" button only if current user is in Admin role.
This is intentionally restricted for testing purposes
so that only Admins can assign/manage claims.
*@
@if (canManageClaims)
{
<a asp-action="ManageClaims" asp-route-id="@u.Id" class="btn btn-sm btn-outline-success">
<i class="bi bi-key me-1"></i> Claims
</a>
}
@*
Show "Manage Roles" button only if user passes ManageRolesPolicy
(requires Permission = AddRole AND EditRole AND DeleteRole).
This ensures only fully privileged users can manage roles.
*@
@if (canManageRoles)
{
<a asp-action="ManageRoles" asp-route-id="@u.Id" class="btn btn-sm btn-outline-dark me-1">
<i class="bi bi-shield-check me-1"></i> Roles
</a>
}
@*
Show "Delete" button only if user passes DeleteUserPolicy
(requires Permission = "DeleteUser").
This prevents unauthorized deletions of user accounts.
*@
@if (canDeleteUser)
{
<a asp-action="Delete" asp-route-id="@u.Id" class="btn btn-sm btn-outline-danger">
<i class="bi bi-trash me-1"></i> Delete
</a>
}
</td>
}
</tr>
}
}
</tbody>
</table>
</div>
</div>
</div>
<partial name="~/Views/Shared/_Pager.cshtml"
model="new PagedResult<object> { Items = Array.Empty<object>(), TotalCount = Model.TotalCount, PageNumber = Model.PageNumber, PageSize = Model.PageSize }" />
</div>
Policy-Based Authorization in ASP.NET Core Identity provides a structured and scalable way to enforce access control by using claims and policies. By defining policies in the Program class file and applying them across controllers, Razor pages, and views, we ensure that permissions are centralized, consistent, and easy to maintain. This approach also enhances flexibility by supporting simple single-claim checks, multiple OR conditions, and complex AND-based requirements.
While policy-based authorization addresses many modern security needs, in real-world applications, we often need the combined strengths of both role-based and claim-based approaches. Roles provide higher-level grouping for easier administration, while claims and policies ensure fine-grained control.
In the next article, I will discuss Hybrid Authorization, i.e., Combining Role-Based and Claim-Based Authorization in ASP.NET Core Identity. In this article, I explain how to Implement Policy-Based Authorization in ASP.NET Core MVC Views with an Example. I hope you enjoy the Policy-Based Authorization article in ASP.NET Core MVC Views.

Watch the Full Tutorial on YouTube!
If you want a complete, step-by-step explanation of how to implement Policy-Based Authorization in ASP.NET Core Identity, don’t miss our in-depth video guide.
👉 Click here to watch now: https://youtu.be/AaZEWa0ZYN0
You’ll learn:
Why policies are better than hard-coded claim checks
How to define and apply policies in Program.cs
Real-world usage in controllers and Razor views
Tips to make your authorization logic clean and scalable
Perfect for developers working on secure ASP.NET Core applications.