Back to: Microsoft Azure Tutorials
Understanding Public, Private, and Hybrid Clouds in Cloud Computing
In this article, I will explain what are Public, Private, and Hybrid Clouds in Cloud Computing. Please read our previous article where we discussed Introduction to Client and Server and Evolution of Azure Cloud. At the end of this article, you will understand the following pointers in detail.
- Understanding Public, Private, and Hybrid Clouds Using a Restaurant Analogy
- Public, Private, and Hybrid Cloud Explained in Cloud Terms
- Differences Between Public Cloud and Private Cloud
- How Azure is Providing Private Cloud, does that mean the server setup is not done in Microsoft Premises?
- Does a Microsoft Representative come to Install Azure Stack Hub on the physical machine in the on-premises machine?
- Can we access both Public and Private cloud through the same Azure Portal?
- What does Azure Arc do as part of a Hybrid Cloud?
- Can on-premise be considered as a Private Cloud?
- CAPEX vs OPEX
- What is Shared Responsibility Model in Azure?
- How does Azure follow a Consumption-Based Model?
Public, Private, and Hybrid Clouds Using a Restaurant Analogy
Using the restaurant analogy, let’s look at public, private, and hybrid cloud types and how they might work in this context:
1. Public Cloud = Food Court Model
- Explanation: In a public cloud, the cloud provider offers shared resources (like servers, storage, etc.) to multiple clients. Each client can rent space on the same server or infrastructure without having to own it. It’s cost-effective and scalable but shared with other users.
- Restaurant Analogy: Imagine you set up a food stall in a food court. You don’t own the space entirely, and many other food stalls are operating in the same food court. You’re using shared resources, like the tables in the common dining area, cleaning services, and security. It’s affordable, convenient, and you only pay for the space you need, but you have to share the space and resources with other businesses.
- Pros: Low cost, no maintenance, highly scalable.
- Cons: Less control and fewer customization options.
2. Private Cloud = Private Restaurant Model
- Explanation: A private cloud is dedicated solely to one organization, providing exclusive access to computing resources. These clouds can be hosted on-site or by a third-party provider but are dedicated only to one client, offering more control, security, and customization.
- Restaurant Analogy: Here, you own or lease an entire restaurant space exclusively for your business. You have complete control over everything—from the kitchen to the dining area. This dedicated setup allows you to customize the ambiance, menu, and layout to meet your exact needs. You have enhanced privacy and control, but it comes with higher costs and maintenance responsibilities.
- Pros: High control, customizable, better security.
- Cons: Higher cost, requires more maintenance.
3. Hybrid Cloud = Combining Food Court and Private Restaurant
- Explanation: A hybrid cloud combines both public and private cloud models. Some of the resources are dedicated solely to you (private), while others are shared (public). This setup allows flexibility, cost-efficiency, and enhanced control over critical operations while using shared resources where practical.
- Restaurant Analogy: Imagine you have a private restaurant space for high-end dining and special services but also maintain a food court stall to offer a more casual, quick-service menu. You use your private space for exclusive dining experiences (private cloud) while leveraging the food court setup to handle high traffic and more casual customers (public cloud). This setup allows you to scale according to customer demand and efficiently use both dedicated and shared resources.
- Pros: Flexible, balances cost with control, can optimize performance based on needs.
Cons: It can be complex to manage both setups.
Public, Private, and Hybrid Cloud Explained in Cloud Terms
Here’s how public, private, and hybrid clouds work in cloud terms with specific examples:
1. Public Cloud
In a public cloud, a third-party provider offers services over the Internet, which are shared among multiple clients. The following are Examples:
- Amazon Web Services (AWS): Offers a wide range of services (compute, storage, database, etc.) available to any organization or individual on a pay-as-you-go basis. Companies like Netflix use AWS for its scalability and extensive global infrastructure.
- Microsoft Azure: Provides various cloud services (like virtual machines, databases, and networking), used by companies like Adobe to deliver creative software via the cloud.
- Google Cloud Platform (GCP): This platform is used by companies like Twitter for its global network, storage, and computing services.
Benefits: Cost-effective, scalable, requires no hardware management.
Limitations: Limited customization and control since the infrastructure is shared.
2. Private Cloud
A private cloud is dedicated to a single organization, providing a high level of control, customization, and security. It can be hosted on-premises or by a third-party provider but remains exclusive to that organization. The following are Examples:
- AWS VPC (Virtual Private Cloud): Although on a public cloud provider, AWS VPC enables customers to create isolated sections within AWS, offering high control and customization.
- Microsoft Azure Stack: Allows companies to deploy Azure services on-premises, giving them private cloud capabilities that integrate with Azure’s public cloud.
- VMware vSphere: Many organizations use VMware’s solutions to set up private clouds on their own servers for dedicated and secure infrastructure, often in fields like finance and healthcare.
Benefits: Enhanced control, customization, and data security.
Limitations: Higher costs and management overhead due to exclusive hardware and infrastructure.
3. Hybrid Cloud
A hybrid cloud combines both public and private clouds, allowing data and applications to be shared between them. This model offers flexibility, enabling companies to scale up using the public cloud for non-sensitive operations while keeping critical workloads on the private cloud. The following are Examples:
- AWS Outposts: Allows companies to use AWS services on-premises while integrating with the public AWS cloud, ideal for applications that need both local processing and access to cloud resources.
- Google Anthos: Provides a platform for managing applications across both on-premises private data centers and Google Cloud, useful for hybrid or multi-cloud setups.
- Azure Arc: Extends Azure services to any infrastructure, enabling companies to manage and deploy resources across both private and public environments, like using Azure for scalability while keeping sensitive data on-premises.
Benefits: Flexibility, optimized costs, better compliance.
Limitations: Complexity in management and integration between public and private environments.
Each of these models serves different organizational needs depending on their requirements for control, scalability, and cost efficiency.
Differences Between Public Cloud and Private Cloud
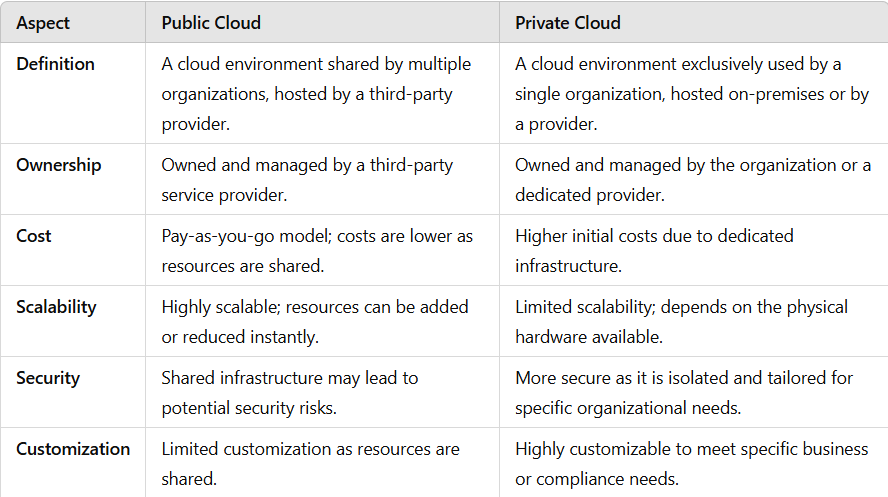
How azure is providing Private cloud, does that mean the server setup is not done in Microsoft Premises?
Azure enables private cloud setups in a couple of ways, depending on where the servers are located and who manages them:
1. Azure Stack (On-Premises Private Cloud)
- How it works: Azure Stack is a product that allows organizations to bring Azure services to their own data centers. This means the private cloud infrastructure (servers, storage, etc.) is set up at the organization’s location (on-premises), but it operates like Azure’s public cloud.
- Who manages it: The organization manages the physical hardware, but they use Azure tools and services to run the cloud environment.
- Example: A bank sets up Azure Stack in its own data center to process sensitive financial transactions securely while still benefiting from Azure’s technology.
2. Azure Dedicated Host (Private Cloud in Microsoft’s Data Centers)
- How it works: Microsoft provides physical servers (dedicated hosts) exclusively for your organization within its own data centers. These servers are not shared with any other Azure customers, making it a private cloud.
- Who manages it: Microsoft manages the physical servers (e.g., maintenance, updates), but you control how they are used, including the operating system, apps, and security configurations.
- Example: A healthcare provider needs to host a private cloud to meet strict data regulations. They rent Azure Dedicated Hosts, ensuring their data is isolated but still benefiting from Microsoft’s infrastructure.
Key Differences
- If Azure Stack is used, the server setup is not on Microsoft’s premises; it’s at your location (or your data center).
- If Azure Dedicated Host is used, the server setup remains on Microsoft’s premises, but it is fully dedicated to your organization.
Does a Microsoft representative come to install Azure Stack Hub on the physical machine in the on-premises machine?
Yes, when deploying Azure Stack Hub, Microsoft-certified professionals or authorized partners handle the installation and setup. Here’s how the process typically works:
Steps for Installing Azure Stack Hub
-
Purchase Azure Stack Hub Integrated System
- Azure Stack Hub is not just software; it requires specialized hardware.
- You purchase the hardware from Microsoft’s approved vendors, such as:
- Dell EMC
- HPE
- Lenovo
- Cisco
- These vendors provide pre-certified, pre-configured physical servers designed to run Azure Stack Hub.
-
Delivery and Installation
- The hardware arrives at your data center.
- A Microsoft-certified team (or vendor representatives) installs and configures the physical machines.
- They ensure:
- Proper cabling and connections.
- Environmental readiness (e.g., cooling, power requirements).
- Rack setup.
-
Software Installation
- Azure Stack Hub software is installed on the hardware by Microsoft-certified professionals.
- Key steps include:
- Installing the Azure Stack Hub operating system.
- Configuring virtualization layers.
- Setting up networking, storage, and security settings.
- Enabling the Azure Portal for local use.
-
Integration with Azure (Optional)
- If the organization wants hybrid cloud capabilities, the team integrates Azure Stack Hub with the public Azure cloud.
- This allows seamless management across both environments.
-
Testing and Handover
- Once installation is complete, the team conducts testing to ensure everything runs smoothly.
- The organization’s IT staff is trained to use Azure Stack Hub tools and services.
Why is Expert Installation Needed?
Azure Stack Hub is a complex system that requires the following:
- Specialized hardware: It only runs on approved, high-performance infrastructure.
- Configuration expertise: Ensuring optimal setup for reliability, security, and compatibility.
- Integration knowledge: Properly connecting the private cloud to Azure’s ecosystem if needed.
Example Scenario: A Bank Installing Azure Stack Hub
- The bank orders Azure Stack Hub hardware from Dell EMC.
- A certified Dell EMC team delivers the servers and installs them in the bank’s data center.
- Azure Stack Hub software is set up by the team, and the bank’s IT team is trained to manage the system.
- The bank starts running its sensitive applications on the private cloud while integrating analytics workloads with Azure’s public cloud.
Key Point: Microsoft doesn’t send its own staff directly. Instead, they work through authorized hardware vendors or partners who handle the installation and provide ongoing support.
Can we access both public and private cloud through the same Azure Portal?
The key benefit of Azure Stack Hub is that it allows you to manage both public Azure and private cloud (on-premises or in your private data center) resources using the same Azure portal.
Shared infrastructure may lead to potential security risks. – How is it possible to do this in public?
1. Data Breaches Due to Misconfiguration
- What happens: Organizations in a public cloud might accidentally misconfigure their resources (e.g., leave storage buckets open or set incorrect permissions). This can expose sensitive data to other users in the cloud or the public internet.
- Example: A company stores customer data on a public cloud service but forgets to restrict access. Another cloud tenant or a malicious actor finds and accesses this data.
2. Hypervisor Vulnerabilities (Virtualization Risks)
- What happens: In a public cloud, multiple virtual machines (VMs) from different customers run on the same physical server using virtualization. If there’s a vulnerability in the hypervisor (the software managing the VMs), a hacker could exploit it to gain access to VMs belonging to other customers.
- Example: A malicious tenant might exploit a hypervisor flaw to access another tenant’s sensitive workloads.
3. Noisy Neighbor Effect
- What happens: In shared infrastructure, one tenant may consume excessive resources (CPU, memory, or bandwidth), affecting the performance or availability of resources for other tenants.
- Example: A neighboring organization runs a resource-intensive application, causing performance issues for your applications hosted on the same cloud infrastructure.
4. Insider Threats
- What happens: Public cloud environments are managed by employees of the cloud provider. A rogue employee or a poorly trained one could accidentally or intentionally access sensitive customer data.
- Example: A cloud provider employee with improper access controls views or leaks customer data.
5. Cross-Tenant Attacks
- What happens: A vulnerability in shared services (e.g., storage, networking) could allow one tenant to interfere with another. Such attacks might exploit weaknesses in multi-tenancy isolation.
- Example: If a shared database or file storage system is misconfigured, a malicious user could access data belonging to other organizations.
6. Lack of Transparency
- What happens: Cloud providers don’t always disclose the full details of how data is stored, processed, or secured in their shared environment. This lack of visibility could leave organizations unaware of certain risks.
- Example: A provider might store backups of your data in a region with weaker privacy regulations without your knowledge.
Let’s discuss some incidents that happened because of potential security risks.
Yes, several real-world security incidents have occurred in public cloud environments due to shared infrastructure, misconfigurations, and vulnerabilities. Here are some notable examples where security glitches in shared cloud environments led to significant breaches or data exposure:
1. Capital One Data Breach (2019)
- Incident: Capital One, a major bank, suffered a data breach in 2019 when a misconfigured firewall on an AWS cloud service allowed a hacker to access sensitive data stored in S3 buckets. Over 100 million customers’ personal information (including credit scores, bank account details, and social security numbers) was compromised.
- Cause: The breach was caused by a misconfigured AWS firewall, which allowed unauthorized access to sensitive data in an Amazon S3 storage bucket.
- Security Glitch: Misconfiguration in shared cloud infrastructure (specifically in access control for S3 storage) led to unrestricted access to sensitive data across multiple tenants, resulting in a massive data leak.
2. AWS S3 Bucket Misconfigurations (Multiple Incidents)
- Incident: AWS S3 (Simple Storage Service) has been the source of multiple incidents due to misconfigured access controls, which allowed sensitive data to be exposed to the public. These incidents have affected various organizations, including healthcare providers, financial institutions, and government agencies. For example, in 2017, Accenture mistakenly exposed 140 GB of sensitive data in an AWS S3 bucket. Similarly, Dow Jones exposed the sensitive data of 2.2 million customers via an unsecured S3 bucket.
- Cause: The root cause was poor configuration of access control lists (ACLs) or public-read access settings on S3 buckets. Many organizations accidentally left their storage open to the public instead of restricting access to authorized users.
- Security Glitch: Public-read access to S3 buckets in a shared cloud environment caused unauthorized access to private data stored by multiple organizations.
3. Google Cloud (Misconfigured IAM Policies)
- Incident: In 2019, a major misconfiguration in Google Cloud IAM (Identity and Access Management) led to multiple organizations inadvertently exposing their Google Cloud storage buckets. Some of the affected organizations included well-known names in retail, financial services, and healthcare.
- Cause: Inadequate configuration of IAM roles and permissions granted access to Google Cloud storage buckets. A common mistake was giving users overly broad access permissions, including the ability to list and read from storage buckets.
- Security Glitch: Misconfigured IAM roles allowed one organization’s cloud resources to be exposed to others in the shared environment, causing data leakage and breaches.
4. Microsoft Azure (Cosmos DB Exposure)
- Incident: In 2020, a security vulnerability in Microsoft Azure’s Cosmos DB database service allowed an attacker to access sensitive data for all users in a specific region. The vulnerability was related to an authentication key used to connect to the Cosmos DB instance, which was accidentally exposed in the Azure portal and shared by a misconfiguration.
- Cause: A misconfigured authentication key exposed the database to unauthorized access by any user with the correct key, leaving potentially millions of Cosmos DB records vulnerable.
- Security Glitch: The shared infrastructure of Azure led to exposed authentication keys being shared among multiple tenants, creating a vulnerability that could be exploited for unauthorized access to sensitive data.
5. GitLab Data Leak (Public Git Repository Misconfiguration)
- Incident: In 2021, a misconfiguration in GitLab’s public repositories exposed sensitive code and private data from a variety of organizations to the public. The leak was caused by incorrect permissions granted to public repositories, which allowed the public to access private repositories and sensitive information.
- Cause: Misconfigured access control settings for repositories allowed them to be viewed publicly, even though they were supposed to be private. This exposed confidential data, source code, and user credentials.
- Security Glitch: A failure in access control management for public resources in the cloud led to unintended exposure of sensitive data across multiple organizations sharing the same infrastructure.
6. Tesla Cloud Misconfiguration (2018)
- Incident: In 2018, Tesla suffered a breach when hackers gained access to its Amazon Web Services (AWS) cloud account due to an exposed administrative console. This allowed the attackers to run cryptocurrency mining operations on Tesla’s cloud infrastructure.
- Cause: The exposure of an internal AWS console due to improper security configurations, specifically misconfigured S3 buckets and lack of proper access management.
- Security Glitch: Tesla’s infrastructure was exposed in a shared cloud environment, allowing unauthorized actors to gain access to critical cloud services and use them for malicious purposes.
Key Takeaways from These Incidents
- Misconfigurations: A common theme in many of these incidents was the misconfiguration of access controls, whether in storage (like S3 buckets), IAM roles, or API keys. In a shared cloud environment, even a small mistake can lead to wide-reaching consequences.
- Shared Responsibility Model: Public cloud providers follow a shared responsibility model, meaning they secure the physical infrastructure and basic services, but customers must secure their applications, data, and configurations. Many breaches were caused by failures in this model.
- Data Exposure: Whether it’s due to improper access settings, API vulnerabilities, or exposed authentication keys, data that should have been protected ended up being exposed to unauthorized parties.
- Cloud Provider Protections: While cloud providers implement strong security measures, users are still responsible for correctly configuring their environments. It is crucial to follow best practices for securing data and applications in a public cloud.
Conclusion
Security issues in shared cloud environments have occurred before, often due to misconfigurations, vulnerabilities in the infrastructure, or improper access controls. These incidents highlight the importance of understanding the shared nature of cloud environments and the need for rigorous configuration management, monitoring, and access control to ensure data remains secure.
What does Azure Arc do as part of a Hybrid cloud?
Azure Arc is a key service from Microsoft that helps manage hybrid cloud environments by extending Azure services and management capabilities to resources outside of Azure, such as on-premises data centers, other public clouds (e.g., AWS, Google Cloud), or even edge devices.
What Azure Arc Does as Part of Hybrid Cloud:
- Centralized Management: Azure Arc allows you to manage and monitor resources across multiple environments (on-premises, Azure, and other public clouds) from a single Azure portal.
- Deploy Azure Services Anywhere: With Azure Arc, you can deploy Azure services like Azure Kubernetes Service (AKS), Azure SQL Database, and Azure App Services on infrastructure outside of Azure (on-premises or other cloud platforms).
- Consistency: It provides consistent management, whether your resources are in Azure or other environments, using tools like Azure Resource Manager (ARM), Azure Security Center, and Azure Policy.
- Hybrid Infrastructure: It allows you to connect on-premises or other cloud-based resources (VMs, Kubernetes clusters, databases) to Azure, enabling hybrid operations without needing to migrate everything to Azure.
Example: A company with on-premises servers can use Azure Arc to manage these servers as if they were in Azure. They can deploy and manage Kubernetes clusters or SQL databases on these on-premises servers using Azure management tools and policies, just like they would with resources inside Azure.
Drawbacks of Hybrid Cloud?
The main drawbacks of a hybrid cloud include the following:
- Complexity: Managing and integrating both on-premises and cloud-based resources can be complex, requiring specialized skills and tools. Data synchronization and consistency across environments can be challenging, especially when data needs to move between private and public clouds.
- Security Concerns: Handling security across multiple environments requires more robust solutions to ensure data privacy, compliance, and access controls. Maintaining consistent security policies across both public and private clouds can be difficult and might lead to potential security gaps.
- Cost Management: While a hybrid cloud can offer flexibility, it can also lead to unpredictable costs. Managing and optimizing costs across different platforms (private and public) might be harder compared to staying with a single cloud provider. Moving workloads between environments can incur extra costs, especially for data transfer.
- Latency Issues: If workloads are split between a private cloud and a public cloud, there may be latency when accessing data or services across these different environments, especially if they are not well connected or located far apart geographically.
- Vendor Lock-in: Even though the hybrid cloud provides flexibility, it can also result in vendor lock-in if one provider’s tools and services are used heavily, limiting the ability to switch providers or move workloads.
- Infrastructure Overhead: Managing both a private cloud and a public cloud means maintaining more infrastructure (hardware, software, networking), which can increase operational overhead and maintenance efforts.
Can on-premise be considered as a private cloud?
Yes, on-premise setups can indeed be considered a form of private cloud—but with some distinctions to keep in mind.
When On-Premises Equals Private Cloud
An on-premises private cloud is when an organization uses its own data center and infrastructure to provide cloud-like services (such as virtualization, automation, and self-service capabilities) exclusively to its internal users. In this case, it behaves similarly to a private cloud:
- Dedicated Resources: The hardware and software are solely for the organization’s use.
- Customization and Control: The organization has complete control over the environment, data, and security.
- Cloud-like Features: The infrastructure may use technologies like virtualization and containerization to create a flexible and scalable environment.
Private Cloud vs. Traditional On-Premises
However, not all on-premises systems qualify as private clouds. Traditional on-premises setups lack certain cloud characteristics, such as:
- Elasticity and Scalability: Private clouds aim to offer on-demand scaling similar to public clouds, which might not be possible with traditional on-premise servers.
- Self-Service Provisioning: A true private cloud allows internal users to provision resources independently through a management portal, as they would in a public cloud.
- Automation and Virtualization: Private clouds often rely on virtualization and automation to distribute resources dynamically, whereas traditional setups may lack this flexibility.
Example
A company using VMware or OpenStack on its own hardware to create virtualized environments for internal use has a private cloud. But if a company simply has a dedicated server room without cloud characteristics like self-service or dynamic scalability, it’s more accurately just on-premises IT than a private cloud.
So, while on-premises can be considered a private cloud, it’s only when it incorporates those cloud-like features.
CAPEX vs OPEX
In the context of Azure and using the restaurant analogy, CapEx (Capital Expenditure) and OpEx (Operational Expenditure) describe two different ways to handle costs, which are especially relevant when moving from traditional IT setups to the cloud.
1. Capital Expenditure (CapEx) = Building Your Own Restaurant
- Explanation: CapEx involves upfront costs for long-term investments, like buying and owning infrastructure. In a traditional IT setup, CapEx would mean purchasing servers, storage, and networking hardware, which are then owned by the organization.
- Restaurant Analogy: Imagine you want to open a restaurant. With CapEx, you buy the building, kitchen equipment (stoves, ovens, refrigerators), tables, chairs, and all other infrastructure you’ll need to run the restaurant. This requires a significant upfront investment, but once purchased, you own all of these resources.
- Azure Context: If an organization decides to buy its own servers and hardware instead of using Azure’s cloud infrastructure, it is making a CapEx investment. It’s a fixed cost, but the organization assumes responsibility for maintenance, upgrades, and management of the physical infrastructure.
- Pros: You own the infrastructure and have full control over it.
- Cons: High initial costs, ongoing maintenance, and depreciation of assets over time.
2. Operational Expenditure (OpEx) = Renting Restaurant Resources as Needed
- Explanation: OpEx is about paying for resources and services as you use them. With Azure, OpEx means renting computing resources, storage, and services on a pay-as-you-go basis, with no need for a large initial investment.
- Restaurant Analogy: Instead of buying a building and all the equipment, you lease a fully-equipped kitchen or rent kitchen resources as needed. For example, you could pay monthly to rent the kitchen space, the stoves, and even the dining area. If you need more tables on busy days, you rent extra for just those times. You pay only for what you use, which is more flexible and can be adjusted based on customer demand.
- Azure Context: Using Azure’s cloud services, you only pay for the computing power, storage, and tools that you need and for the time that you need them. When you scale up or down, your costs adjust accordingly. Azure takes care of maintenance and infrastructure upgrades.
- Pros: Lower upfront costs, flexibility, scalability, and no maintenance burden.
- Cons: Potential for ongoing costs to exceed expectations if not managed carefully.
Summary:
- CapEx in Azure: If you were to handle all the infrastructure yourself, purchasing hardware, storage, and networking equipment (equivalent to owning the restaurant) would be a CapEx approach.
- OpEx in Azure: Leveraging Azure’s cloud services to “rent” resources as needed, paying only for what you use, is an OpEx approach (like renting a restaurant space instead of buying).
In the Azure world, adopting an OpEx model allows businesses to avoid high upfront costs and offers flexibility to scale resources based on demand. This shift from CapEx to OpEx is one of the main advantages of moving to the cloud.
Shared Responsibility Model
In Azure’s shared responsibility model, the cloud provider (Microsoft Azure) and the customer share the responsibilities for security, management, and infrastructure, each taking care of different aspects of the environment. Using our restaurant analogy, here’s how the shared responsibility model works:
Shared Responsibility Model in Azure:
In the restaurant context, think of this as the division of tasks and responsibilities between the restaurant owner (the customer) and the building owner/landlord (Azure).
1. Azure’s Responsibilities = The Building and Facility Maintenance
- Explanation: Azure, as the cloud provider, is responsible for the security and upkeep of the physical infrastructure, network, and foundational elements on which cloud services are built. This includes the data center, physical servers, and the base infrastructure.
- Restaurant Analogy: The building owner or landlord (Azure) is responsible for maintaining the restaurant building’s structure, ensuring the utilities (water, electricity, gas) work, and managing the security of the property, like installing security cameras and alarms in the common areas. The building owner ensures a safe, functional environment so the restaurant can operate smoothly.
- Examples in Azure:
- Physical security of data centers.
- Managing hardware and network infrastructure.
- Ensuring foundational security, like data encryption at rest for hardware.
2. Customer’s Responsibilities = Running and Managing the Restaurant
- Explanation: The customer (you, the restaurant operator) is responsible for what you do inside the rented environment. In Azure, this means managing applications, data, access controls, and any configurations related to the specific cloud services you use.
- Restaurant Analogy: As the restaurant owner, you’re responsible for day-to-day operations inside the restaurant. This includes hiring and managing staff, securing ingredients (data), preparing food (applications), handling customer data, and ensuring internal security measures (e.g., keeping your storage area locked and managing access for employees). If a recipe or ingredient gets compromised, that responsibility lies with the restaurant owner, not the building landlord.
- Examples in Azure:
- Configuring access controls and managing identity (e.g., Azure Active Directory).
- Securing data by managing encryption keys and backups.
- Setting up firewall rules and network security for virtual machines.
- Ensuring proper application security and patching software.
Division of Responsibilities Based on Service Model (IaaS, PaaS, SaaS). In Azure’s shared responsibility model, Azure ensures the restaurant building is safe, functional, and secure while you, as the customer, handle everything inside your restaurant space to ensure the experience, safety, and management of your unique services and data. This division changes based on the cloud model, with more responsibility shifting to Azure as you move from IaaS to SaaS.
How does Azure follow a Consumption-Based Model?
In Azure, the Consumption-Based Model is a pricing structure where you pay only for the cloud resources and services you use. This is like a “pay-as-you-go” system, similar to ordering services or ingredients in a restaurant based on demand.
Consumption-Based Model in Azure Using the Restaurant Analogy
Imagine running a restaurant where you only pay for the ingredients, kitchen equipment, and staff you actually use, rather than paying a fixed amount regardless of how busy or quiet the restaurant is.
-
Pay-as-You-Go Resources = Ordering Ingredients and Resources as Needed
- Explanation: In Azure, the consumption-based model lets you pay for compute power, storage, and networking resources only when you need them.
- Restaurant Analogy: Instead of stocking up on ingredients in bulk, you order fresh ingredients daily based on the actual number of customers and their orders. On a busy day, you order more ingredients, while on a quiet day, you order less. This reduces waste and keeps costs tied to actual demand.
- Azure Example: If you need more virtual machines or storage space for a busy period (e.g., a special event), you pay for the extra resources only for that time. Once the demand decreases, you scale down and pay less.
-
Scaling Resources = Adding or Removing Tables and Staff as Needed
- Explanation: Azure’s consumption model allows for easy scalability. You can add resources during peak times and reduce them when they’re no longer needed.
- Restaurant Analogy: Imagine you’re a restaurant owner who can instantly add more tables and hire extra staff during rush hours or weekends. When customer flow returns to normal, you reduce the number of tables and staff to save costs. You aren’t paying for unused tables or idle staff.
- Azure Example: When traffic to an application spikes, you can increase the number of virtual machines or server power to handle the load, and reduce them afterward.
-
No Upfront Commitment = Avoiding Long-Term Contracts for Ingredients or Equipment
- Explanation: In Azure’s consumption model, there’s no need for a big upfront investment; instead, costs adjust with use.
- Restaurant Analogy: You don’t need to lock into long-term contracts with suppliers or buy all kitchen equipment outright. Instead, you rent or pay as needed, which is especially helpful if your restaurant business is seasonal.
- Azure Example: For temporary or experimental projects, you can run them in Azure without committing to long-term infrastructure purchases. When the project ends, the costs stop.
-
Billing Based on Use = Paying Only for What’s Served
- Explanation: Azure tracks usage of resources down to the hour, minute, or even second, billing you only for what you consume.
- Restaurant Analogy: Imagine you only pay your suppliers for each dish served rather than paying for all ingredients upfront. If you don’t make a particular dish, there’s no cost for its ingredients.
- Azure Example: If you turn on a virtual machine for one hour, you’re billed for just that hour. If you don’t use the virtual machine, you’re not charged.
Summary:
In the Consumption-Based Model on Azure, you pay for resources as needed, just like a restaurant that orders ingredients and hires staff based on customer demand. This model helps reduce costs by aligning expenses directly with usage, offering flexibility to adjust resources based on real-time demand and eliminating upfront investment in unused resources.
